Consider the following scenario:

The user P with smart card SC makes a request "print A" to W1. Before W1 can complete the request it needs to read the object A, so W1 issues a request "read A" to the server WS. The request is processed by the reference monitor at the server (assume it contains an ACL that allows P to read A). Should the reference monitor approve the request from W1?
It is time to put on our "paranoid" hats. We want to know whether the request is really made on behalf of P. We ensure this in the following way: we create a delegation certificate D1:[W1 for P]SC. This is certificate is just the bit string W1 for P which is prepared by W1 at login time and sent to the user who signs it with the smart card SC and returns it back to W1. The meaning of the certificate is that W1 can now make requests on behalf of P, or "speak for P".
We use the certificate as follows:
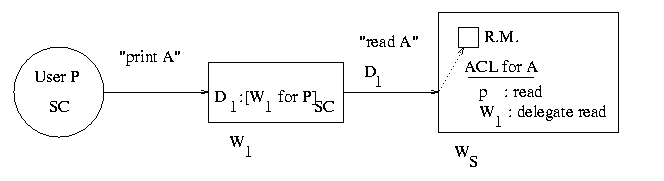
The user makes a request "print A" to W1 as before. When W1 makes its request to WS, D1 is forwarded along with the request. Now the reference monitor can verify the authenticity of the certificate using the user's well-known public key and approve the request. Note that:
- We require that the ACL for A contains an entry "W1: delegate read". This is in accordance with the principle of least privilege: only some workstations are allowed to speak for P so we explicitly check for that right.
- The channel between W1 and WS needs to be integrity-protected, otherwise an attacker can alter the read request, which might still be approved (since it is accompanied by the delegation certificate D1).
- If W1 is subverted, then the security of the system is compromised. If the user P does not trust W1 to be secure then P should not give a delegation certificate to W1.

This leads to the need for the delegation certificate D2. It is just a bit string that W2 sends to W1 who signs it with its private key and sends it back to W2; W2 can then forward it along with the request. The reference monitor reasons as follows: a request is coming from W2 with a certificate D2:[W2 for P]W1 , signed by W1. The reference monitor honors this certificate if and only if W2 has the "delegate read" right and we can make sure that W1 speaks for P. The reference monitor then looks at D1 and since D1 is signed by the smart card and W1 has the "delegate read" right, it is satisfied that the request is legitimately coming from P. Since P has the "read" right, the request is approved.
Note that instead of D2 we could have used D2´:[W2 for W1]W1. However, such a certificate is much less restrictive and therefore not a good idea.
Typically, each workstation involved in implementing a service will keep cached copies of all delegation certificates for client systems, so it can forward these copies along with requests to any servers that it must contact in order to satisfy a request for service.
When a delegation certificate is no longer needed (e.g. the user logs out), the system should no longer have the right to represent the user. But how do we revoke these certificates?
Let us start with some simple (almost) solutions:
- Include timeouts in certificates.
There is a trade-off here.
If we set the timeout
too high, then there is a chance that an attacker might be able to
make use of the certificate after the user logs out but before it
expires. If we set the timeout too low, then the certificate might
expire during an interactive session, forcing the user to create a new
certificate (i.e. inconvenience). There is no general solution to this
problem.
- Deletion. Upon logout, the user can instruct all workstation that might have cached certificates to delete them. But how does the user know that they are really deleted? The certificates might have been intercepted by an attacker who can store them indefinitely.
More concretely, in our example, the scheme changes as follows:
- W1 generates a (private, public) key pair (k, K);
- the certificate D1 becomes [K, W1 for P]SC;
- when challenged to prove that it holds the private key for the public key K, W1 can do that;
- to revoke D1, W1 forgets the private key k -- D1 no longer works since nobody else has k.