
Javasoft/Sun Flaw #25: The Vacuum Exploit
June 23, 1997
The exploit takes advantage of a verifier flaw in JDK 1.1.2 and
Hotjava. We have constructed a rogue applet that is in violation of
the Java Virtual Machine specification but can nevertheless evade the
JDK 1.1 verifier. Once a user downloads this applet, it
starts retrieving textual information from the browser. It sends this
information back to the originating server, as shown with the thick
arrow in Figure 1. The applet performs the information transfer in
the background in an uninterruptible way that can only be terminated
by killing the Hotjava browser.

Figure 1. Exploit.
Once the
Hotjava user clicks on a page containing a rogue applet, his privacy
is compromised. The rogue applet scans memory for
private information and sends its findings to a central site.
Our example exploit contains a progress monitor class which
periodically queries the central site and displays to the user the
information that has been leaked out so far. Figure 2 shows a typical
screen capture, showing information including name, hardware information
and configuration settings, captured within minutes after invoking the
rogue applet. In real life, a malicious applet would not provide a
progress monitor and would give no indication of the security breach
to the user.
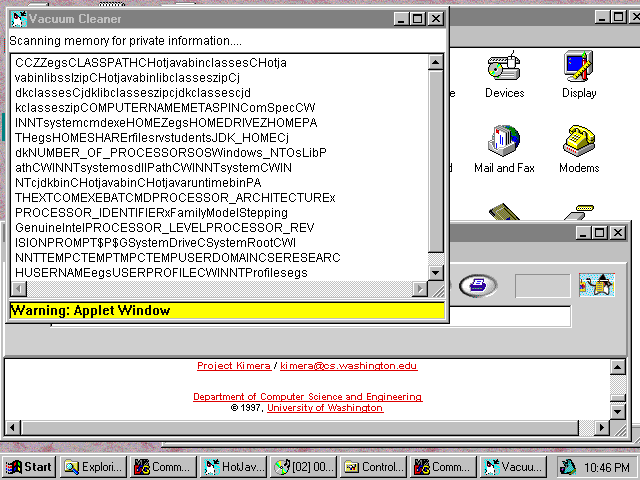
Figure 2. Screen capture of the exploit in progress.
The rogue applet has stolen the name, hardware
information and configuration settings from the user's private
environment. The heap, containing browser history, cache and
passwords, is next.
We suggest that users who use JDK 1.1.2 and JDK 1.1 based
products such as Hotjava in safety, security or privacy-critical
applications obtain and apply all relevant security patches from
Javasoft. Alternatively or in addition, users may
want to send untrusted Java code through a strong
verifier before admitting it into their systems.
Emin Gün Sirer &
Sean McDirmid &
Brian Bershad



